iam in cloud computing Iam employ secure
If you are looking for What to Expect: Future Trends in Identity & Access Management you’ve came to the right page. We have 9 Images about What to Expect: Future Trends in Identity & Access Management like What to Expect: Future Trends in Identity & Access Management, Manage IAM User Access for a Multi-Account Architecture – LearnAWS.cloud and also Cloud Computing Basics: A Complete Guide | iStats.com. Here it is:
What To Expect: Future Trends In Identity & Access Management
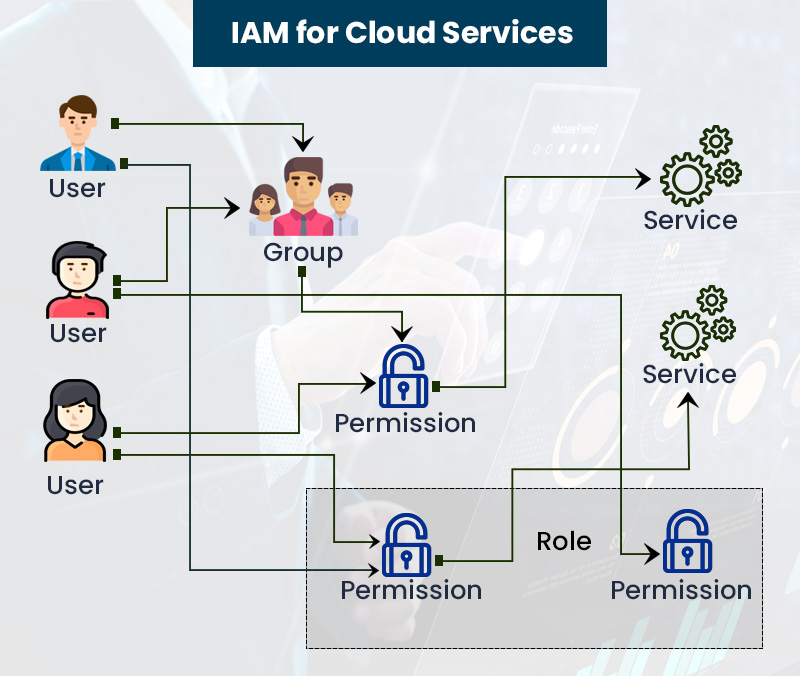
www.veritis.com
iam employ secure
IAM Security – CloudCodes IAM Solution For Data Access & Security
www.cloudcodes.com
iam security cloud identity access management data secure enterprises balanced helps computing
Types Of Cloud Computing Service Models – Prix Constantin
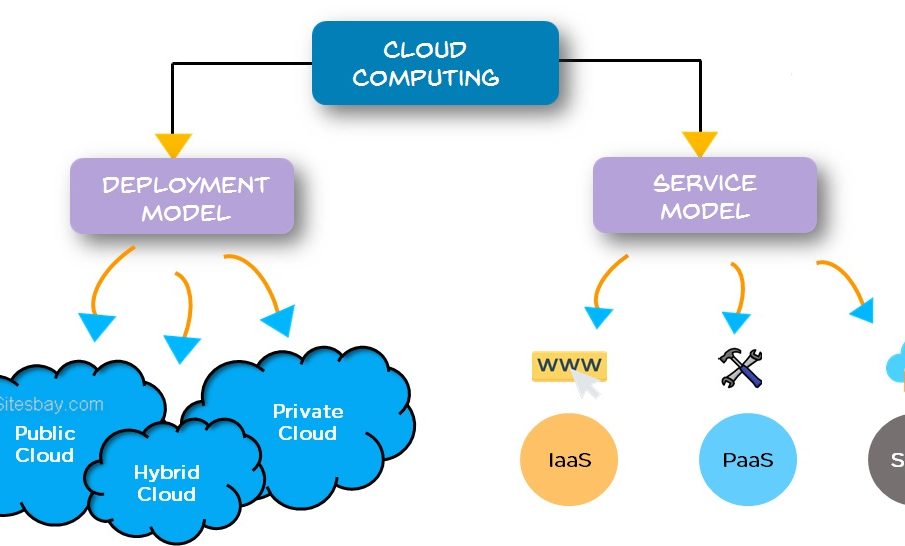
www.prixconstantin.com
computing sorts iaas
Nothing Cloudy About The Identity Access Management (IAM) Future
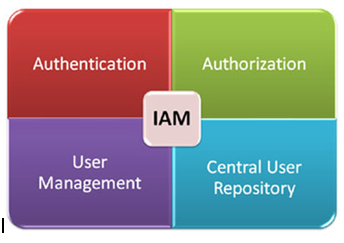
blog.sysfore.com
iam management access cloud identity future cloudy nothing evolution secure business join
Deploying Identity And Access Management (IAM) Infrastructure In The
www.hubcitymedia.com
iam infrastructure deployment deploying
IAM Cloud | Software Cogs For Your Cloud Machine

www.iamcloud.com
iam
Manage IAM User Access For A Multi-Account Architecture – LearnAWS.cloud

learnaws.cloud
iam
4 Tips To Maximize Your IAM Strategy In The Cloud | Sirius Computer

www.siriuscom.com
iam lifecycle siriuscom
Cloud Computing Basics: A Complete Guide | IStats.com

www.istats.com
istats
Cloud computing basics: a complete guide. What to expect: future trends in identity & access management. Types of cloud computing service models
if you are looking "id":498,"keyword_id":null,"name":"iam in cloud computing","scraped_at":"2023-03-12 18:37:20","created_at":"2023-03-12T18:37:17.000000Z","updated_at":"2023-03-12T18:37:20.000000Z","images":["id":4465,"keyword_id":498,"url":"https:\/\/www.veritis.com\/wp-content\/uploads\/2020\/08\/iam-for-cloud-services.jpg","link":"https:\/\/www.veritis.com\/blog\/what-to-expect-future-trends-in-identity-and-access-management\/","title":"What to Expect: Future Trends in Identity & Access Management","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.O2NFkSX2fiVB0VhIYoLgGQHaGQ&pid=15.1","size":"800 x 676 \u00b7 jpeg","desc":"iam employ secure","filetype":"jpg","width":800,"height":676,"domain":"www.veritis.com","created_at":null,"updated_at":null,"id":4466,"keyword_id":498,"url":"https:\/\/i1.wp.com\/learnaws.cloud\/wp-content\/uploads\/2020\/02\/iam-user-multi-account.png?fit=960%2C560&ssl=1","link":"https:\/\/learnaws.cloud\/aws\/manage-iam-user-access-for-a-multi-account-architecture\/","title":"Manage IAM User Access for a Multi-Account Architecture – LearnAWS.cloud","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.6fC23vRNTRkGhc7rzx0GUQHaEU&pid=15.1","size":"960 x 560 \u00b7 png","desc":"iam","filetype":"png","width":960,"height":560,"domain":"learnaws.cloud","created_at":null,"updated_at":null,"id":4467,"keyword_id":498,"url":"https:\/\/www.siriuscom.com\/wp-content\/uploads\/2019\/04\/IAM-User-Lifecycle-Graphic-800×450.jpg","link":"https:\/\/www.siriuscom.com\/2019\/04\/4-tips-to-maximize-your-iam-strategy-in-the-cloud\/","title":"4 Tips to Maximize Your IAM Strategy in the Cloud ,"id":4468,"keyword_id":498,"url":"http:\/\/blog.sysfore.com\/wp-content\/uploads\/2016\/03\/Cloud-IAM.png","link":"https:\/\/blog.sysfore.com\/nothing-cloudy-about-identity-access-management-iam-future\/","title":"Nothing Cloudy About The Identity Access Management (IAM) future","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.cLVmF3qnkqYhRfBhs-mMWgHaFO&pid=15.1","size":"344 x 243 \u00b7 png","desc":"iam management access cloud identity future cloudy nothing evolution secure business join","filetype":"png","width":344,"height":243,"domain":"blog.sysfore.com","created_at":null,"updated_at":null,"id":4469,"keyword_id":498,"url":"https:\/\/www.istats.com\/wp-content\/uploads\/2018\/06\/cloud-computing-basics.jpeg","link":"https:\/\/www.istats.com\/470\/cloud-computing-basics-a-complete-guide\/","title":"Cloud Computing Basics: A Complete Guide ,"id":4470,"keyword_id":498,"url":"https:\/\/www.iamcloud.com\/wp-content\/uploads\/2020\/01\/4.png","link":"https:\/\/www.iamcloud.com\/","title":"IAM Cloud ,"id":4471,"keyword_id":498,"url":"https:\/\/www.cloudcodes.com\/blog\/wp-content\/uploads\/2018\/02\/iam-data-security.jpg","link":"https:\/\/www.cloudcodes.com\/blog\/iam-security-balanced-data-security.html","title":"IAM Security – CloudCodes IAM Solution For Data Access & Security","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.s9IKeWiUV0OQ3GA9NhryqAHaFS&pid=15.1","size":"560 x 400 \u00b7 jpeg","desc":"iam security cloud identity access management data secure enterprises balanced helps computing","filetype":"jpg","width":560,"height":400,"domain":"www.cloudcodes.com","created_at":null,"updated_at":null,"id":4472,"keyword_id":498,"url":"https:\/\/www.prixconstantin.com\/wp-content\/uploads\/2020\/07\/c-1-905×546.jpg","link":"https:\/\/www.prixconstantin.com\/types-of-cloud-computing-service-models\/","title":"Types of Cloud Computing Service Models – Prix Constantin","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.iOVb2PfUQG0FWpNeRQybhgHaEd&pid=15.1","size":"905 x 546 \u00b7 jpeg","desc":"computing sorts iaas","filetype":"jpg","width":905,"height":546,"domain":"www.prixconstantin.com","created_at":null,"updated_at":null,"id":4473,"keyword_id":498,"url":"https:\/\/images.squarespace-cdn.com\/content\/v1\/59cc0d69268b9646d2e7db65\/1583419963002-GISCAZRO9GK80CD5MUMO\/ke17ZwdGBToddI8pDm48kJiz0-5RQxyREcUG2X9xr3pZw-zPPgdn4jUwVcJE1ZvWQUxwkmyExglNqGp0IvTJZUJFbgE-7XRK3dMEBRBhUpwA6gfprmjI7XkcA4un0CPoKA9xtGFrXJGVPDSvzCdUoifVIsmdv6ptiGl3yzPFHGQ\/Identity+and+Access+Management+(IAM)+Reference+Architecture","link":"https:\/\/www.hubcitymedia.com\/blog\/deploying-identity-and-access-management-iam-infrastructure-in-the-cloud-pt1-planning","title":"Deploying Identity and Access Management (IAM) Infrastructure in the","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.SjzBCvphA371yPlEG5SL1QHaFj&pid=15.1","size":"720 x 540 \u00b7 png","desc":"iam infrastructure deployment deploying","filetype":"png","width":720,"height":540,"domain":"www.hubcitymedia.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about iam in cloud computing Iam employ secure. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.

+Reference+Architecture)





