cloud computing vulnerabilities Vulnerabilities computing taxonomy understanding contributing
If you are searching about Understanding Cloud Computing Vulnerabilities you’ve visit to the right place. We have 9 Pictures about Understanding Cloud Computing Vulnerabilities like Cloud Computing Threats: Beyond Vulnerabilities, Cloud Computing Vulnerabilities – Compass Cyber Security and also Cloud Computing Threats: Beyond Vulnerabilities. Read more:
Understanding Cloud Computing Vulnerabilities

www.infoq.com
computing cloud vulnerabilities
Cloud Computing Vulnerabilities – Compass Cyber Security

www.compasscyber.com
cloud computing vulnerabilities july
Top Cloud Threats Your Business Should Look Out For (Infographic

www.pinterest.com
transcosmos
Cloud Security Vulnerabilities: A Step-by-Step Plan For Quelling

newcontext.com
vulnerabilities wolke nuvola arcanum quelling threats computing bleuwire collegamento environments hardening dunklem globales goldtext glo padlock hält vorhängeschloß virtuellen schirmes
Understanding Cloud Computing Vulnerabilities

www.infoq.com
vulnerabilities computing taxonomy understanding contributing
CLOUD COMPUTING SECURITY ISSUES, CHALLENGES AND SOLUTION – E2MATRIX

www.e2matrix.com
issues e2matrix dummies vulnerabilities
The Different Types Of Cloud Computing Explained In Plain English. Www

www.pinterest.com
assurance hosting
Understanding Cloud Computing Vulnerabilities
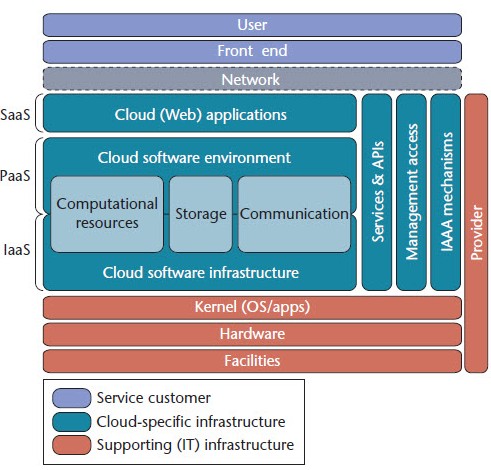
www.infoq.com
cloud vulnerabilities computing architecture reference overview figure ieee components security service specific map
Cloud Computing Threats: Beyond Vulnerabilities
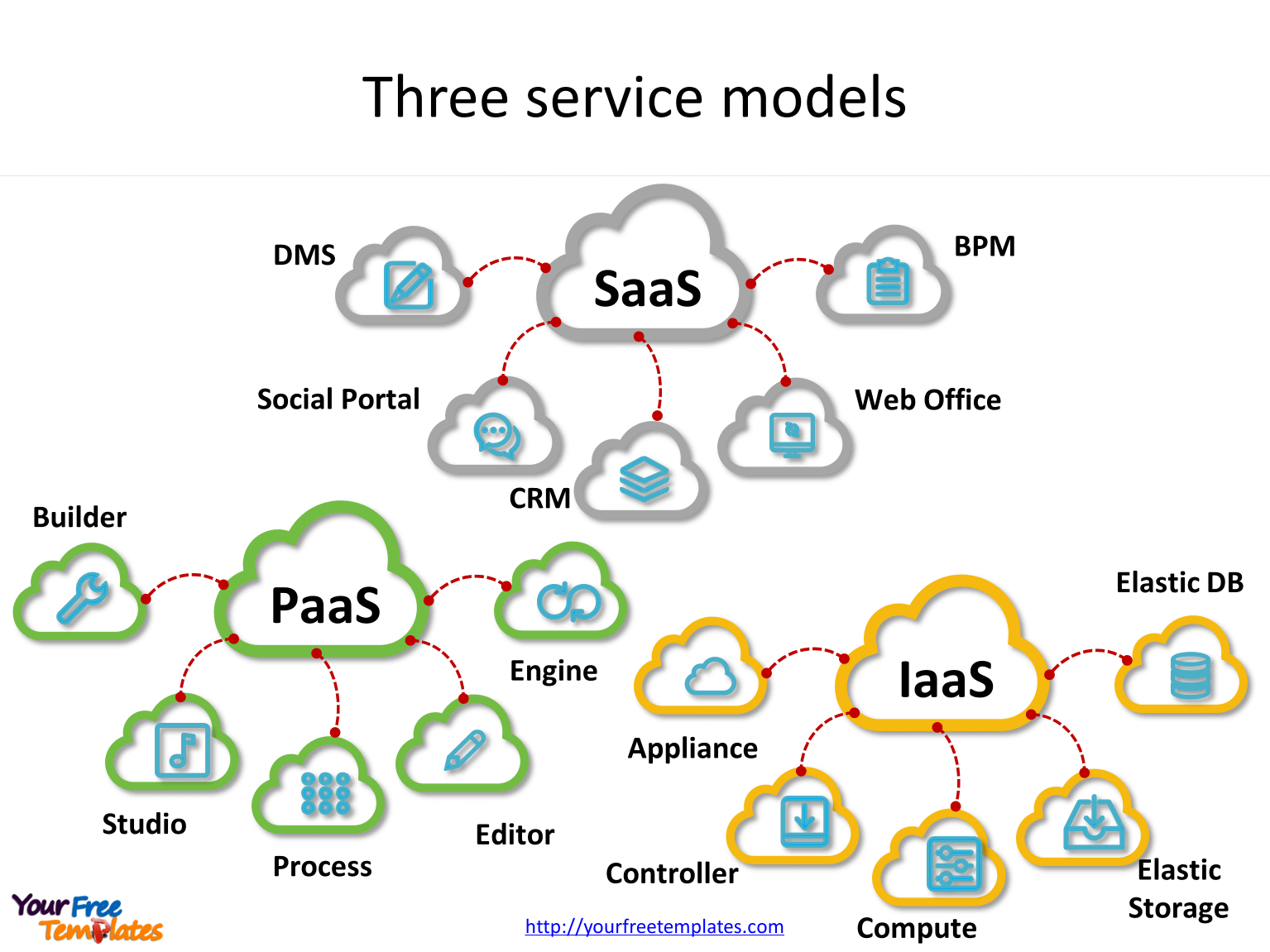
heimdalsecurity.com
cloud computing powerpoint service vulnerabilities threats models templates model slide beyond mention among benefits
Cloud vulnerabilities computing architecture reference overview figure ieee components security service specific map. Top cloud threats your business should look out for (infographic. Cloud computing vulnerabilities july
if you are looking "id":401,"keyword_id":null,"name":"cloud computing vulnerabilities","scraped_at":"2023-03-12 18:37:20","created_at":"2023-03-12T18:37:17.000000Z","updated_at":"2023-03-12T18:37:20.000000Z","images":["id":3556,"keyword_id":401,"url":"https:\/\/heimdalsecurity.com\/blog\/wp-content\/uploads\/Cloud_computing_for_service_model-e1511673879328.png","link":"https:\/\/heimdalsecurity.com\/blog\/cloud-computing-threats\/","title":"Cloud Computing Threats: Beyond Vulnerabilities","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.qU-yef0m0xKsy-1cGMGtMgHaFj&pid=15.1","size":"1535 x 1151 \u00b7 png","desc":"cloud computing powerpoint service vulnerabilities threats models templates model slide beyond mention among benefits","filetype":"png","width":1535,"height":1151,"domain":"heimdalsecurity.com","created_at":null,"updated_at":null,"id":3557,"keyword_id":401,"url":"https:\/\/www.compasscyber.com\/wp-content\/uploads\/2017\/07\/cloud-computing-850×372.png","link":"https:\/\/www.compasscyber.com\/blog\/cloud-computing-vulnerabilities\/","title":"Cloud Computing Vulnerabilities – Compass Cyber Security","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.yHxhrK4a32QvM8JfV9dMxgHaDP&pid=15.1","size":"850 x 372 \u00b7 png","desc":"cloud computing vulnerabilities july","filetype":"png","width":850,"height":372,"domain":"www.compasscyber.com","created_at":null,"updated_at":null,"id":3558,"keyword_id":401,"url":"https:\/\/res.infoq.com\/articles\/ieee-cloud-computing-vulnerabilities\/en\/resources\/figure1large.jpg","link":"http:\/\/www.infoq.com\/articles\/ieee-cloud-computing-vulnerabilities","title":"Understanding Cloud Computing Vulnerabilities","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.4VispW9zGSBQolUAXv-Y8wHaDP&pid=15.1","size":"903 x 396 \u00b7 jpeg","desc":"vulnerabilities computing taxonomy understanding contributing","filetype":"jpg","width":903,"height":396,"domain":"www.infoq.com","created_at":null,"updated_at":null,"id":3559,"keyword_id":401,"url":"http:\/\/www.e2matrix.com\/blog\/wp-content\/uploads\/2017\/10\/1.jpg","link":"http:\/\/www.e2matrix.com\/blog\/2017\/10\/13\/cloud-computing-security-issues-challenges-and-solution\/","title":"CLOUD COMPUTING SECURITY ISSUES, CHALLENGES AND SOLUTION – E2MATRIX","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.0a_1nDMim-WuFCum-QtPoQAAAA&pid=15.1","size":"439 x 235 \u00b7 jpeg","desc":"issues e2matrix dummies vulnerabilities","filetype":"jpg","width":439,"height":235,"domain":"www.e2matrix.com","created_at":null,"updated_at":null,"id":3560,"keyword_id":401,"url":"https:\/\/res.infoq.com\/articles\/ieee-cloud-computing-vulnerabilities\/en\/resources\/figure2.jpg","link":"https:\/\/www.infoq.com\/articles\/ieee-cloud-computing-vulnerabilities\/","title":"Understanding Cloud Computing Vulnerabilities","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.Tm_GJUQX_Om56Hb0j2AbMAHaHF&pid=15.1","size":"491 x 470 \u00b7 jpeg","desc":"cloud vulnerabilities computing architecture reference overview figure ieee components security service specific map","filetype":"jpg","width":491,"height":470,"domain":"www.infoq.com","created_at":null,"updated_at":null,"id":3561,"keyword_id":401,"url":"https:\/\/i.pinimg.com\/originals\/49\/06\/70\/49067064265ae9c277c47b61223f7f02.png","link":"https:\/\/www.pinterest.com\/pin\/635992778602211088\/","title":"Top Cloud Threats Your Business Should Look Out For (Infographic","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.oaL3t1CC65A313H74RETewHanH&pid=15.1","size":"800 x 4225 \u00b7 png","desc":"transcosmos","filetype":"png","width":800,"height":4225,"domain":"www.pinterest.com","created_at":null,"updated_at":null,"id":3562,"keyword_id":401,"url":"https:\/\/res.infoq.com\/articles\/ieee-cloud-computing-vulnerabilities\/en\/smallimage\/small image.jpg","link":"https:\/\/www.infoq.com\/articles\/ieee-cloud-computing-vulnerabilities","title":"Understanding Cloud Computing Vulnerabilities","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.DjSU2Up5kNo64C4iwuJYtQAAAA&pid=15.1","size":"100 x 95 \u00b7 jpeg","desc":"computing cloud vulnerabilities","filetype":"jpg","width":100,"height":95,"domain":"www.infoq.com","created_at":null,"updated_at":null,"id":3563,"keyword_id":401,"url":"https:\/\/i.pinimg.com\/736x\/0a\/16\/4b\/0a164b775ffbe31b53fd1a9b7e97666d–cloud-computing-different-types-of.jpg","link":"https:\/\/www.pinterest.com\/pin\/180144053819762633\/","title":"The different types of cloud computing explained in plain english. www","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.OAyMa_33HfjNnf-ZUi4D7wHaLc&pid=15.1","size":"736 x 1137 \u00b7 jpeg","desc":"assurance hosting","filetype":"jpg","width":736,"height":1137,"domain":"www.pinterest.com","created_at":null,"updated_at":null,"id":3564,"keyword_id":401,"url":"https:\/\/1o94re31z2r53ujw5331m3or-wpengine.netdna-ssl.com\/wp-content\/uploads\/2020\/10\/cloud-security-vulnerabilities-800×534.jpg","link":"https:\/\/newcontext.com\/cloud-security-vulnerabilities-step-by-step-plan-for-quelling-threats-nc\/","title":"Cloud Security Vulnerabilities: A Step-by-Step Plan for Quelling","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.GePICd_dXB1A-R-1iMxgJQHaE8&pid=15.1","size":"800 x 534 \u00b7 jpeg","desc":"vulnerabilities wolke nuvola arcanum quelling threats computing bleuwire collegamento environments hardening dunklem globales goldtext glo padlock h\u00e4lt vorh\u00e4ngeschlo\u00df virtuellen schirmes","filetype":"jpg","width":800,"height":534,"domain":"newcontext.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about cloud computing vulnerabilities Vulnerabilities computing taxonomy understanding contributing. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.






