cloud computing vs cyber security Cloud computing v.s. cyber security
If you are searching about Differences between Traditional PC Vs Cloud Computer. www.connectio.in you’ve came to the right page. We have 9 Images about Differences between Traditional PC Vs Cloud Computer. www.connectio.in like Differences between Traditional PC Vs Cloud Computer. www.connectio.in, Cloud Computing v.s. Cyber Security and also Cloud Computing v.s. Cyber Security. Here you go:
Differences Between Traditional PC Vs Cloud Computer. Www.connectio.in

www.pinterest.com
cloud computing traditional vs security between cyber services computer differences
PPT – Cyber Security And Cloud Computing PowerPoint Presentation, Free

www.slideserve.com
cyber computing cloud security ppt powerpoint presentation skip
Cloud Computing V.s. Cyber Security

www.slideshare.net
cloud security cyber computing slideshare
Cloud Computing V.s. Cyber Security
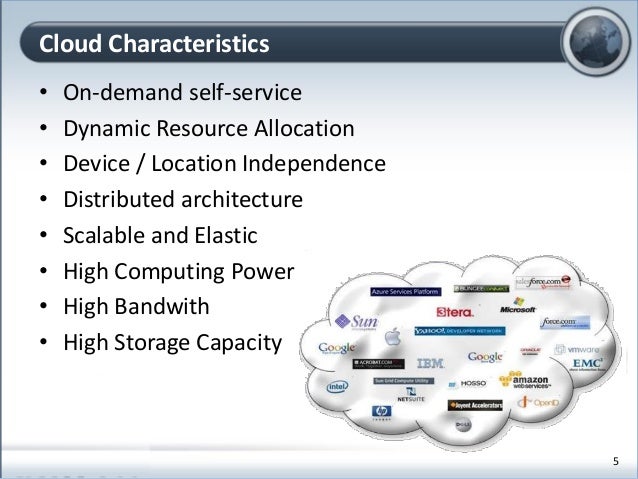
www.slideshare.net
Cloud Computing V.s. Cyber Security
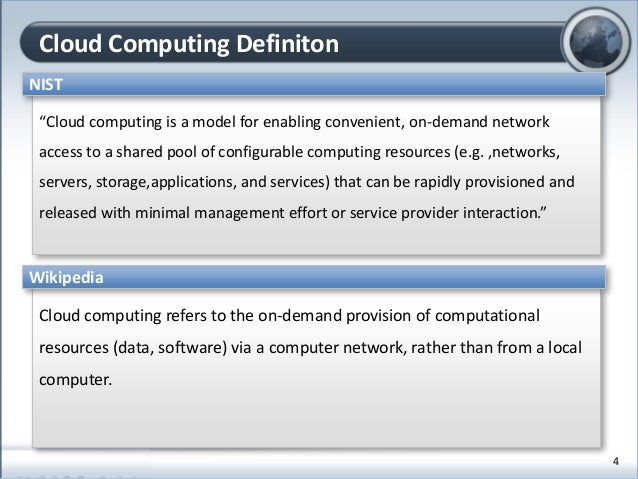
www.slideshare.net
cyber
How To Approach Cloud Computing And Cyber Security In 2018 | T/DG Blog

blog.thedigitalgroup.com
computing cloud cyber approach security dec danish wadhwa author views added
Cloud Computing V.s. Cyber Security
www.slideshare.net
cyber
Cloud Computing V.s. Cyber Security
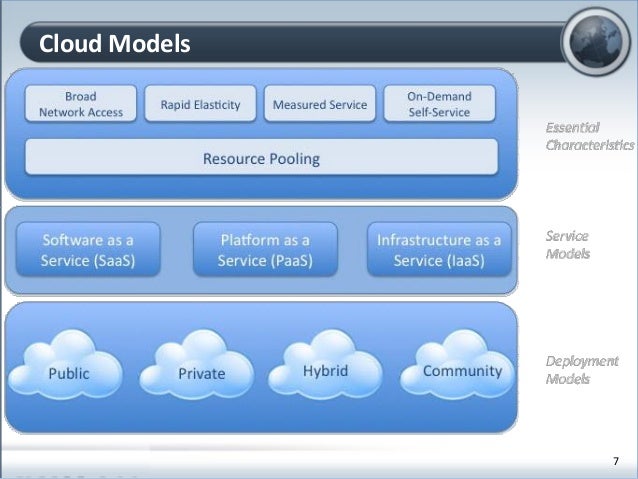
www.slideshare.net
Infrastructure Versus Information Cyber Security In The Cloud

www.archive360.com
infrastructure archive360
Cloud computing v.s. cyber security. Differences between traditional pc vs cloud computer. www.connectio.in. Cloud computing v.s. cyber security
if you are looking "id":395,"keyword_id":null,"name":"cloud computing vs cyber security","scraped_at":"2023-03-12 18:37:20","created_at":"2023-03-12T18:37:17.000000Z","updated_at":"2023-03-12T18:37:20.000000Z","images":["id":3547,"keyword_id":395,"url":"https:\/\/i.pinimg.com\/736x\/b8\/c0\/99\/b8c099bd05ab4a5829faa4d0858a804a.jpg","link":"https:\/\/www.pinterest.com\/pin\/668714244648681351\/","title":"Differences between Traditional PC Vs Cloud Computer. www.connectio.in","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.iEyGhfIWOaiWnllj6tuadwHaHW&pid=15.1","size":"736 x 731 \u00b7 jpeg","desc":"cloud computing traditional vs security between cyber services computer differences","filetype":"jpg","width":736,"height":731,"domain":"www.pinterest.com","created_at":null,"updated_at":null,"id":3548,"keyword_id":395,"url":"https:\/\/image.slidesharecdn.com\/bahtiyar-150630120853-lva1-app6891\/95\/cloud-computing-vs-cyber-security-5-638.jpg?cb=1468272534","link":"https:\/\/www.slideshare.net\/BahtiyarBircan\/cloud-computing-vs-cyber-security","title":"Cloud Computing v.s. Cyber Security","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.0VON0qYr-2RCPP78nwSr1gHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":3549,"keyword_id":395,"url":"https:\/\/image.slidesharecdn.com\/bahtiyar-150630120853-lva1-app6891\/95\/cloud-computing-vs-cyber-security-2-638.jpg?cb=1468272534","link":"https:\/\/www.slideshare.net\/BahtiyarBircan\/cloud-computing-vs-cyber-security","title":"Cloud Computing v.s. Cyber Security","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.mqLHnJ5sO4x19lMdK-eHTwHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"cyber","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":3550,"keyword_id":395,"url":"https:\/\/image.slidesharecdn.com\/bahtiyar-150630120853-lva1-app6891\/95\/cloud-computing-vs-cyber-security-4-638.jpg?cb=1468272534","link":"https:\/\/www.slideshare.net\/BahtiyarBircan\/cloud-computing-vs-cyber-security","title":"Cloud Computing v.s. Cyber Security","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.3crXyTsGOvf1xugz6yU1dQHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"cyber","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":3551,"keyword_id":395,"url":"https:\/\/image.slidesharecdn.com\/bahtiyar-150630120853-lva1-app6891\/95\/cloud-computing-vs-cyber-security-7-638.jpg?cb=1468272534","link":"https:\/\/www.slideshare.net\/BahtiyarBircan\/cloud-computing-vs-cyber-security","title":"Cloud Computing v.s. Cyber Security","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.yBBAVRI-V0ZomFkpgatf0AHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":3552,"keyword_id":395,"url":"https:\/\/image.slidesharecdn.com\/bahtiyar-150630120853-lva1-app6891\/95\/cloud-computing-vs-cyber-security-1-638.jpg?cb=1468272534","link":"https:\/\/www.slideshare.net\/BahtiyarBircan\/cloud-computing-vs-cyber-security","title":"Cloud Computing v.s. Cyber Security","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.OV73lagW463Dc3EALs6UzgHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"cloud security cyber computing slideshare","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":3553,"keyword_id":395,"url":"https:\/\/image1.slideserve.com\/2254313\/cyber-security-and-cloud-computing-n.jpg","link":"https:\/\/www.slideserve.com\/oakley\/cyber-security-and-cloud-computing","title":"PPT – Cyber Security and Cloud Computing PowerPoint Presentation, free","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.Y9YalN2Gb_UNiuxbEa34bAHaFj&pid=15.1","size":"720 x 540 \u00b7 jpeg","desc":"cyber computing cloud security ppt powerpoint presentation skip","filetype":"jpg","width":720,"height":540,"domain":"www.slideserve.com","created_at":null,"updated_at":null,"id":3554,"keyword_id":395,"url":"https:\/\/blog.thedigitalgroup.com\/assets\/uploads\/Approach-Cloud-Computing-and-Cyber-Security-in-2018-5-Dec-DigitalThoughts.jpg","link":"https:\/\/blog.thedigitalgroup.com\/how-to-approach-cloud-computing-and-cyber-security-in-2018","title":"How to Approach Cloud Computing and Cyber Security in 2018 ,"id":3555,"keyword_id":395,"url":"https:\/\/www.archive360.com\/hs-fs\/hubfs\/Cloud_Cyber_security-1.png?width=730&height=365&name=Cloud_Cyber_security-1.png","link":"https:\/\/www.archive360.com\/blog\/infrastructure-versus-information-cyber-security-in-the-cloud","title":"Infrastructure versus Information Cyber Security in the Cloud","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP._E8N38I6rmrdStP8l1AX6gHaD_&pid=15.1","size":"676 x 365 \u00b7 png","desc":"infrastructure archive360","filetype":"png","width":676,"height":365,"domain":"www.archive360.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about cloud computing vs cyber security Cloud computing v.s. cyber security. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.






