cloud computing that is secure is known as Cloud computing security
If you are looking for Cloud Computing Security you’ve visit to the right page. We have 9 Pics about Cloud Computing Security like Is cloud computing secure? – Quora, A cloud built on integrated security – Intelligent CIO Africa and also A cloud built on integrated security – Intelligent CIO Africa. Here it is:
Cloud Computing Security
![]()
worldinformatixcs.com
cloud computing security public services hosting technology works platform web companies computer sap where pricing solution internet business
A Cloud Built On Integrated Security – Intelligent CIO Africa

www.intelligentcio.com
tco intelligent environments
Secure Cloud Computing Stock Photo – Download Image Now – Cloud
www.istockphoto.com
cloud computing secure network computer cloudscape communication
How Cloud Computing Is Shaping The Future Of Technology – Movie TV Tech
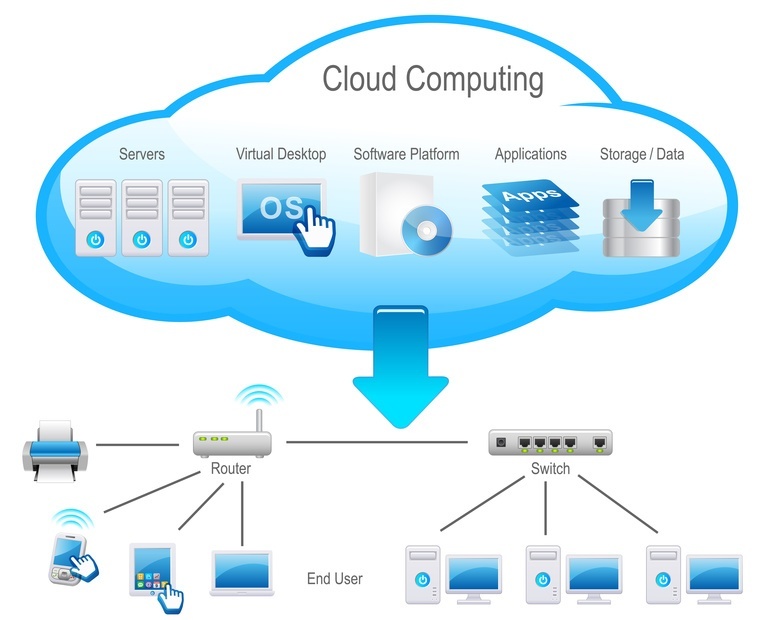
movietvtechgeeks.com
cloud computing technology example data shaping work future storage management services movie practice why computer microsoft network
Is Cloud Computing Secure? – Quora
www.quora.com
cloud computing aws azure security microsoft umbrella cisco secure vs storage key
Cisco Extends SD-WAN Options With AWS, Azure Hybrid-cloud Integration

www.networkworld.com
azure cyber adobestock cloudsecurity alerts ampere chip cisco extends staggering roadmap juniper sase
Secure Cloud Computing — Stock Vector © Koctia #46687331
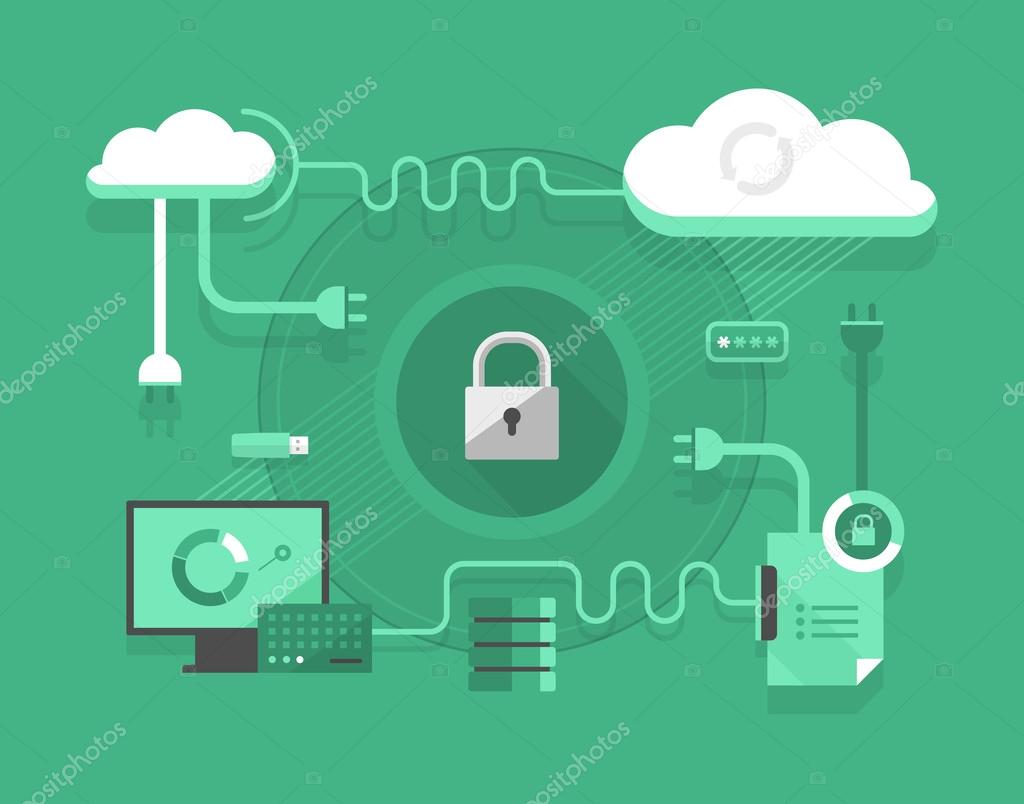
depositphotos.com
secure vpn computing cloud illustration step gdpr depositphotos reading nordvpn compliant becoming guide submeter information system meter protect data
Emerging Trends Of Cloud Computing: A Brief Guide : TTP

techtrendspro.com
computing emerging brief removed
Addressing The Biggest Risks To Cloud Computing Security

www.startexsoftware.com
cloud computing security risk management addressing risks biggest saas
Computing emerging brief removed. Cloud computing aws azure security microsoft umbrella cisco secure vs storage key. Secure cloud computing — stock vector © koctia #46687331
if you are looking "id":373,"keyword_id":null,"name":"cloud computing that is secure is known as","scraped_at":"2023-03-12 18:37:20","created_at":"2023-03-12T18:37:17.000000Z","updated_at":"2023-03-12T18:37:20.000000Z","images":["id":3358,"keyword_id":373,"url":"https:\/\/qph.fs.quoracdn.net\/main-qimg-439326b47f31de14ab123501a9634f9b","link":"https:\/\/www.quora.com\/Is-cloud-computing-secure","title":"Is cloud computing secure? – Quora","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.Q5MmtH8x3hSrEjUBqWNPmwHaFj&pid=15.1","size":"602 x 452 \u00b7 jpeg","desc":"cloud computing aws azure security microsoft umbrella cisco secure vs storage key","filetype":"jpg","width":602,"height":452,"domain":"www.quora.com","created_at":null,"updated_at":null,"id":3359,"keyword_id":373,"url":"https:\/\/www.intelligentcio.com\/africa\/wp-content\/uploads\/sites\/5\/2019\/12\/Cloud-security-1000-pic-scaled.jpg","link":"https:\/\/www.intelligentcio.com\/africa\/2019\/12\/19\/a-cloud-built-on-integrated-security\/","title":"A cloud built on integrated security – Intelligent CIO Africa","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.NtnGt2vHTdbaUzq5CqUHyQHaE8&pid=15.1","size":"2560 x 1707 \u00b7 jpeg","desc":"tco intelligent environments","filetype":"jpg","width":2560,"height":1707,"domain":"www.intelligentcio.com","created_at":null,"updated_at":null,"id":3360,"keyword_id":373,"url":"https:\/\/images.idgesg.net\/images\/article\/2020\/08\/secure-data-network-digital-cloud-computing-cyber-security-concept-picture-id1157887211-100855471-large.jpg","link":"https:\/\/www.networkworld.com\/article\/3576002\/cisco-extends-sd-wan-options-with-aws-azure-hybrid-cloud-integration.html","title":"Cisco extends SD-WAN options with AWS, Azure hybrid-cloud integration","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.nvtSiZTL361j_X51byRC_wHaE8&pid=15.1","size":"1200 x 800 \u00b7 jpeg","desc":"azure cyber adobestock cloudsecurity alerts ampere chip cisco extends staggering roadmap juniper sase","filetype":"jpg","width":1200,"height":800,"domain":"www.networkworld.com","created_at":null,"updated_at":null,"id":3361,"keyword_id":373,"url":"http:\/\/movietvtechgeeks.com\/wp-content\/uploads\/2015\/05\/cloud-computing-in-action-images-2015.jpg","link":"https:\/\/movietvtechgeeks.com\/how-cloud-computing-is-shaping-the-future-of-technology\/","title":"How Cloud Computing is shaping the future of technology – Movie TV Tech","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.RI2vERIQH6h6wiR0XxhbugHaF7&pid=15.1","size":"775 x 620 \u00b7 jpeg","desc":"cloud computing technology example data shaping work future storage management services movie practice why computer microsoft network","filetype":"jpg","width":775,"height":620,"domain":"movietvtechgeeks.com","created_at":null,"updated_at":null,"id":3362,"keyword_id":373,"url":"https:\/\/www.startexsoftware.com\/hubfs\/cloud computing security.png","link":"https:\/\/www.startexsoftware.com\/blog\/addressing-the-biggest-risks-to-cloud-computing-security","title":"Addressing the Biggest Risks to Cloud Computing Security","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.vtmM-xDhtRzj-NuzpuqZzwHaE8&pid=15.1","size":"1920 x 1281 \u00b7 png","desc":"cloud computing security risk management addressing risks biggest saas","filetype":"png","width":1920,"height":1281,"domain":"www.startexsoftware.com","created_at":null,"updated_at":null,"id":3363,"keyword_id":373,"url":"https:\/\/st.depositphotos.com\/1768806\/4668\/v\/950\/depositphotos_46687331-stock-illustration-secure-cloud-computing.jpg","link":"https:\/\/depositphotos.com\/46687331\/stock-illustration-secure-cloud-computing.html","title":"Secure Cloud Computing \u2014 Stock Vector \u00a9 koctia #46687331","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.as89M9cN4foQHST5Z2CmNAHaF0&pid=15.1","size":"1024 x 804 \u00b7 jpeg","desc":"secure vpn computing cloud illustration step gdpr depositphotos reading nordvpn compliant becoming guide submeter information system meter protect data","filetype":"jpg","width":1024,"height":804,"domain":"depositphotos.com","created_at":null,"updated_at":null,"id":3364,"keyword_id":373,"url":"https:\/\/cdn.shortpixel.ai\/client\/q_lossy,ret_img,w_500\/https:\/\/worldinformatixcs.com\/wp-content\/uploads\/2018\/01\/ccs.jpg","link":"https:\/\/worldinformatixcs.com\/cloud-computing-security\/","title":"Cloud Computing Security","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.n28AMfvDL3CnIWdt72aEdwHaFb&pid=15.1","size":"500 x 367 \u00b7 jpeg","desc":"cloud computing security public services hosting technology works platform web companies computer sap where pricing solution internet business","filetype":"jpg","width":500,"height":367,"domain":"worldinformatixcs.com","created_at":null,"updated_at":null,"id":3365,"keyword_id":373,"url":"https:\/\/media.istockphoto.com\/photos\/secure-cloud-computing-picture-id530450177","link":"https:\/\/www.istockphoto.com\/photo\/secure-cloud-computing-gm530450177-54562564","title":"Secure Cloud Computing Stock Photo – Download Image Now – Cloud","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP._cLftFdNo4vYTVuofL7tMAHaE8&pid=15.1","size":"1024 x 683 \u00b7 jpeg","desc":"cloud computing secure network computer cloudscape communication","filetype":"jpg","width":1024,"height":683,"domain":"www.istockphoto.com","created_at":null,"updated_at":null,"id":3366,"keyword_id":373,"url":"https:\/\/techtrendspro.com\/wp-content\/uploads\/2019\/06\/1395-Converted-min.jpg","link":"https:\/\/techtrendspro.com\/emerging-trends-cloud-computing\/","title":"Emerging Trends of Cloud Computing: A Brief Guide : TTP","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.n4KQ3-CrKIY7HF1p_DPlNQHaEo&pid=15.1","size":"1920 x 1200 \u00b7 jpeg","desc":"computing emerging brief removed","filetype":"jpg","width":1920,"height":1200,"domain":"techtrendspro.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about cloud computing that is secure is known as Cloud computing security. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.







