cloud computing or cyber security What does cyber security consist of in the cloud?
If you are searching about What is cloud security? you’ve visit to the right place. We have 9 Pictures about What is cloud security? like What is cloud security?, The Truth About Cloud Security – Cyber Security Services Seattle and also CloudBric: The Future of Cloud Computing and Cyber Security.. Here it is:
What Is Cloud Security?

www.kaspersky.com
computing kaspersky
CloudBric: The Future Of Cloud Computing And Cyber Security.

medium.com
security cyber future cloud computing
The Truth About Cloud Security – Cyber Security Services Seattle

cybersecurityservicesseattle.com
cloud security truth services cyber
The Shift In Security Operations In A Multi-Cloud World | 2018-03-01

www.securitymagazine.com
cloud security cyber operations shift multi
Cloud Computing Security – Netsonic's Blog

blog.netsonic.net
cloud computing security
Cloud Computing – 初识4 Cyber Security
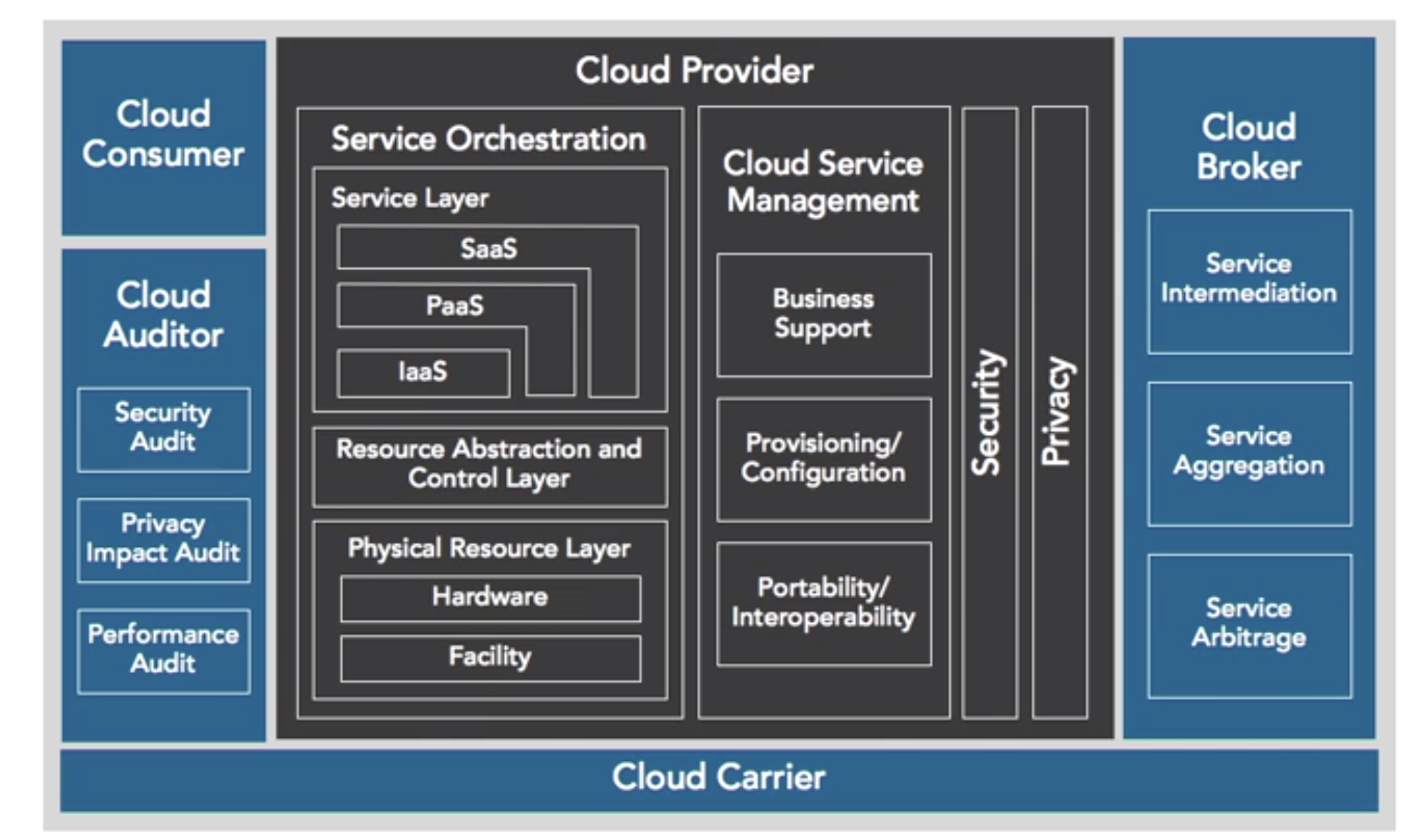
hiwanglong.github.io
What Does Cyber Security Consist Of In The Cloud?

www.ecpi.edu
cyber security cloud consist does ecpi
Secure Data Network Digital Cloud Computing Cyber Security Concept
www.istockphoto.com
cloud computing security cyber secure network concept digital data
Cloud Based Cyber Security / Cloud-Based Cyber Security — An

mangapss.blogspot.com
Computing kaspersky. Cloud computing security. Cloud computing security cyber secure network concept digital data
if you are looking "id":322,"keyword_id":null,"name":"cloud computing or cyber security","scraped_at":"2023-03-12 18:37:20","created_at":"2023-03-12T18:37:17.000000Z","updated_at":"2023-03-12T18:37:20.000000Z","images":["id":2890,"keyword_id":322,"url":"https:\/\/www.kaspersky.com\/content\/en-global\/images\/repository\/isc\/2020\/what-is-cloud-security01.jpg","link":"https:\/\/www.kaspersky.com\/resource-center\/definitions\/what-is-cloud-security","title":"What is cloud security?","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.5tS2YXcIusyrxpQhayJWyQHaEL&pid=15.1","size":"710 x 400 \u00b7 jpeg","desc":"computing kaspersky","filetype":"jpg","width":710,"height":400,"domain":"www.kaspersky.com","created_at":null,"updated_at":null,"id":2891,"keyword_id":322,"url":"https:\/\/cybersecurityservicesseattle.com\/wp-content\/uploads\/2020\/06\/cloudsecurity.jpeg","link":"https:\/\/cybersecurityservicesseattle.com\/the-truth-about-cloud-security\/","title":"The Truth About Cloud Security – Cyber Security Services Seattle","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.W7v7tPW43_o5IHgurzUjjAHaDN&pid=15.1","size":"1013 x 440 \u00b7 jpeg","desc":"cloud security truth services cyber","filetype":"jpg","width":1013,"height":440,"domain":"cybersecurityservicesseattle.com","created_at":null,"updated_at":null,"id":2892,"keyword_id":322,"url":"https:\/\/media.istockphoto.com\/photos\/secure-data-network-digital-cloud-computing-cyber-security-concept-picture-id1157887211?k=6&m=1157887211&s=170667a&w=0&h=hT1YV5R8NEg87fuKIoZWRNKOvh2sJgltGTou4sm8MF8=","link":"https:\/\/www.istockphoto.com\/photo\/secure-data-network-digital-cloud-computing-cyber-security-concept-earth-element-gm1157887211-316086282","title":"Secure Data Network Digital Cloud Computing Cyber Security Concept","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.MlbOdt4Uy-f6PzYtGroQ7QHaEK&pid=15.1","size":"553 x 311 \u00b7 jpeg","desc":"cloud computing security cyber secure network concept digital data","filetype":"jpg","width":553,"height":311,"domain":"www.istockphoto.com","created_at":null,"updated_at":null,"id":2893,"keyword_id":322,"url":"https:\/\/blog.netsonic.net\/wp-content\/uploads\/2015\/01\/cloud-computing-security1.png","link":"https:\/\/blog.netsonic.net\/cloud-computing-security\/","title":"Cloud Computing Security – Netsonic's Blog","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.9n9MC2IQwi9RBCCjudWQZgHaHa&pid=15.1","size":"800 x 800 \u00b7 png","desc":"cloud computing security","filetype":"png","width":800,"height":800,"domain":"blog.netsonic.net","created_at":null,"updated_at":null,"id":2894,"keyword_id":322,"url":"https:\/\/www.securitymagazine.com\/ext\/resources\/secenews\/2018\/cloud-900-cyber.jpg?1519933374","link":"https:\/\/www.securitymagazine.com\/blogs\/14-security-blog\/post\/88787-the-shift-in-security-operations-in-a-multi-cloud-world","title":"The Shift in Security Operations in a Multi-Cloud World ,"id":2895,"keyword_id":322,"url":"https:\/\/www.ecpi.edu\/sites\/default\/files\/ecpi_61.png","link":"https:\/\/www.ecpi.edu\/blog\/what-does-cyber-security-consist-of-in-the-cloud","title":"What Does Cyber Security Consist of in the Cloud?","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.HR1RGrebfKxsOyCTNpCuNgHaFj&pid=15.1","size":"1024 x 768 \u00b7 png","desc":"cyber security cloud consist does ecpi","filetype":"png","width":1024,"height":768,"domain":"www.ecpi.edu","created_at":null,"updated_at":null,"id":2896,"keyword_id":322,"url":"https:\/\/thumbs.dreamstime.com\/z\/cloud-computer-cyber-security-virtual-screen-computing-immersive-interface-circuits-blurred-lines-code-concept-data-151866904.jpg","link":"https:\/\/mangapss.blogspot.com\/2021\/05\/cloud-based-cyber-security-cloud-based.html","title":"Cloud Based Cyber Security \/ Cloud-Based Cyber Security — An","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.zjRLKIV6xDQffZnUZ4UN0AHaFW&pid=15.1","size":"1600 x 1156 \u00b7 jpeg","desc":"","filetype":"jpg","width":1600,"height":1156,"domain":"mangapss.blogspot.com","created_at":null,"updated_at":null,"id":2897,"keyword_id":322,"url":"https:\/\/cdn-images-1.medium.com\/max\/1600\/1*mX_pxODIHNKDgLJ2yMH0vA.jpeg","link":"https:\/\/medium.com\/datadriveninvestor\/cloudbric-the-future-of-cloud-computing-and-cyber-security-5033d0bf8e75","title":"CloudBric: The Future of Cloud Computing and Cyber Security.","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.FYZmxa2_D70hEK0bJ_OVfgHaE7&pid=15.1","size":"1600 x 1066 \u00b7 jpeg","desc":"security cyber future cloud computing","filetype":"jpg","width":1600,"height":1066,"domain":"medium.com","created_at":null,"updated_at":null,"id":2898,"keyword_id":322,"url":"https:\/\/hiwanglong.github.io\/images\/cloudSecurity\/1-cloudArchi.png","link":"https:\/\/hiwanglong.github.io\/2019\/05\/cloud-computing-\u521d\u8bc64-cyber-security\/","title":"Cloud Computing – \u521d\u8bc64 cyber security","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.g2dxRI-l01uaLUbfdC-kFAHaEZ&pid=15.1","size":"1982 x 1178 \u00b7 png","desc":"","filetype":"png","width":1982,"height":1178,"domain":"hiwanglong.github.io","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about cloud computing or cyber security What does cyber security consist of in the cloud?. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.







