campus fp vistalegre big data & cybersecurity technology Data technology futuristic advanced woman business big master mining concept cyber security role china analytics predictive cybersecurity unity3d college fba
If you are searching about Cybersecurity in the Age of Big Data – iTrain (M) Sdn Bhd you’ve came to the right place. We have 9 Pictures about Cybersecurity in the Age of Big Data – iTrain (M) Sdn Bhd like Cybersecurity Technology – Copiah-Lincoln Community College, The Role of Big Data in Cyber Security and also Openwork BPM | 2020 all'insegna di Big Data & Cybersecurity. Read more:
Cybersecurity In The Age Of Big Data – ITrain (M) Sdn Bhd

www.itrain.com.my
cybersecurity data big age itrain start
Openwork BPM | 2020 All'insegna Di Big Data & Cybersecurity

www.openworkbpm.com
cybersecurity insegna informatica sicurezza dei
The Role Of Big Data In Cyber Security

blog.augustschell.com
data technology futuristic advanced woman business big master mining concept cyber security role china analytics predictive cybersecurity unity3d college fba
Stay Safe, Offline & Online: Cybersecurity Checklist – Infographic
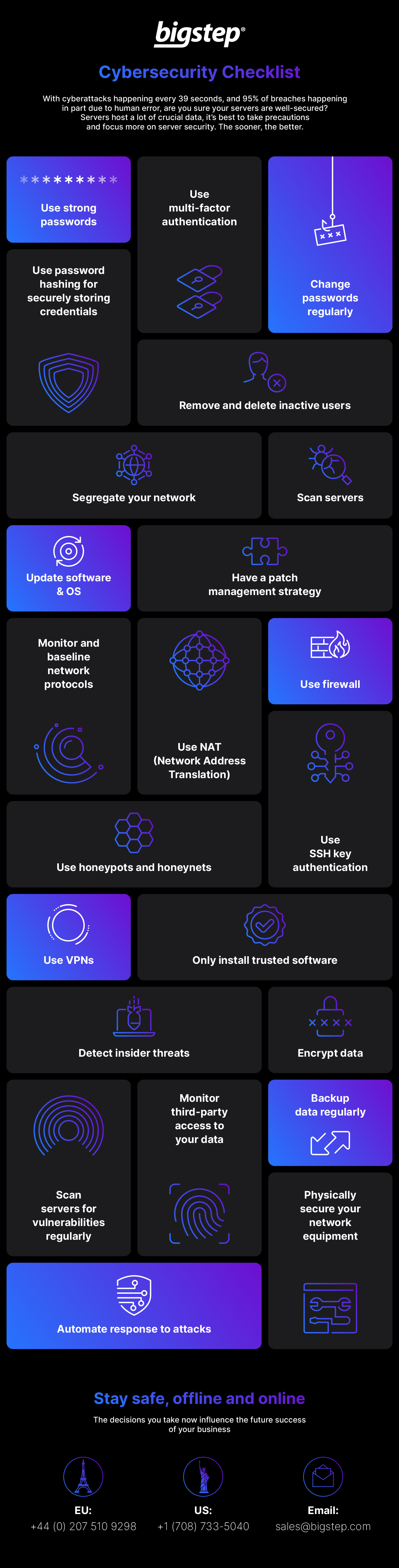
bigstep.com
cybersecurity bigstep
Three Simple And Effective Cybersecurity Basics For Off-The-Grid Living

www.offthegridnews.com
cybersecurity basics simple effective grid three living off longer option
Big Data & Cybersecurity – EForensics

eforensicsmag.com
cybersecurity data big
Cybersecurity Big Data: самые крупные утечки биометрических данных

www.bigdataschool.ru
Big Data And Cyber Security: Together, Stronger | Kratikal

kratikal.com
data big security cyber together stronger
Cybersecurity Technology – Copiah-Lincoln Community College

www.colin.edu
cybersecurity technology information general colin
Cybersecurity in the age of big data. Cybersecurity data big. Cybersecurity big data: самые крупные утечки биометрических данных
if you are looking "id":232,"keyword_id":null,"name":"campus fp vistalegre big data & cybersecurity technology","scraped_at":"2023-03-11 07:57:06","created_at":"2023-03-11T07:57:01.000000Z","updated_at":"2023-03-11T07:57:06.000000Z","images":["id":2116,"keyword_id":232,"url":"https:\/\/www.colin.edu\/colin\/cache\/file\/F0650F8C-155D-F311-6C774FF99A3EE12C_page-pic.jpg","link":"https:\/\/www.colin.edu\/majors-programs\/career-technical\/information-systems-and-business\/cybersecurity-technology\/","title":"Cybersecurity Technology – Copiah-Lincoln Community College","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.6CwIXp20ocVFQWMVhHvRWAHaDK&pid=15.1","size":"1170 x 500 \u00b7 jpeg","desc":"cybersecurity technology information general colin","filetype":"jpg","width":1170,"height":500,"domain":"www.colin.edu","created_at":null,"updated_at":null,"id":2117,"keyword_id":232,"url":"https:\/\/blog.augustschell.com\/hubfs\/big-data-cybersecurity.jpg#keepProtocol","link":"https:\/\/blog.augustschell.com\/the-role-of-big-data-in-cyber-security","title":"The Role of Big Data in Cyber Security","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.tQgEOJOeHjdrsFt0RzgRfwHaHa&pid=15.1","size":"1500 x 1500 \u00b7 jpeg","desc":"data technology futuristic advanced woman business big master mining concept cyber security role china analytics predictive cybersecurity unity3d college fba","filetype":"jpg","width":1500,"height":1500,"domain":"blog.augustschell.com","created_at":null,"updated_at":null, 2020 all'insegna di Big Data & Cybersecurity","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.YZcoPRxmvAYiijNRUYaFfAHaD3&pid=15.1","size":"800 x 418 \u00b7 png","desc":"cybersecurity insegna informatica sicurezza dei","filetype":"png","width":800,"height":418,"domain":"www.openworkbpm.com","created_at":null,"updated_at":null,"id":2119,"keyword_id":232,"url":"https:\/\/www.offthegridnews.com\/wp-content\/uploads\/2018\/08\/AdobeStock_141951442.jpeg","link":"https:\/\/www.offthegridnews.com\/privacy\/cybersecurity-basics\/","title":"Three Simple And Effective Cybersecurity Basics For Off-The-Grid Living","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.Vi6VNCi7h8x4pBnOD884_gHaEA&pid=15.1","size":"6500 x 3512 \u00b7 jpeg","desc":"cybersecurity basics simple effective grid three living off longer option","filetype":"jpg","width":6500,"height":3512,"domain":"www.offthegridnews.com","created_at":null,"updated_at":null,"id":2120,"keyword_id":232,"url":"https:\/\/www.itrain.com.my\/wp-content\/uploads\/2019\/08\/iTrain-Cybersecurity-Big-Data-2019-02-1024×525.jpg","link":"https:\/\/www.itrain.com.my\/events\/cybersecurity-in-the-age-of-big-data\/","title":"Cybersecurity in the Age of Big Data – iTrain (M) Sdn Bhd","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.HBMR2e7wxBeDTF1dGEk0FAHaDz&pid=15.1","size":"1024 x 525 \u00b7 jpeg","desc":"cybersecurity data big age itrain start","filetype":"jpg","width":1024,"height":525,"domain":"www.itrain.com.my","created_at":null,"updated_at":null,"id":2121,"keyword_id":232,"url":"https:\/\/kratikal.com\/blog\/wp-content\/uploads\/2017\/06\/Big-data-1024×1024.jpg","link":"https:\/\/kratikal.com\/blog\/big-data-cyber-security-together\/","title":"Big Data and Cyber security: Together, Stronger ,"id":2122,"keyword_id":232,"url":"https:\/\/eforensicsmag.com\/wp-content\/uploads\/2017\/09\/efnewworkshop1.jpg","link":"https:\/\/eforensicsmag.com\/product\/big-data-cybersecurity\/","title":"Big Data & Cybersecurity – eForensics","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.13PfufWevm2hwHDyLqxZJgHaKe&pid=15.1","size":"2480 x 3508 \u00b7 jpeg","desc":"cybersecurity data big","filetype":"jpg","width":2480,"height":3508,"domain":"eforensicsmag.com","created_at":null,"updated_at":null,"id":2123,"keyword_id":232,"url":"https:\/\/bigstep.com\/assets\/images\/cybersecurity-checklist-infographic.png","link":"https:\/\/bigstep.com\/blog\/stay-safe-offline-online-cybersecurity-checklist-infographic","title":"Stay Safe, Offline & Online: Cybersecurity Checklist \u2013 Infographic","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.vhfiWho8X5tJZIJH9XkOywHadH&pid=15.1","size":"1220 x 4796 \u00b7 png","desc":"cybersecurity bigstep","filetype":"png","width":1220,"height":4796,"domain":"bigstep.com","created_at":null,"updated_at":null,"id":2124,"keyword_id":232,"url":"https:\/\/www.bigdataschool.ru\/wp-content\/uploads\/2020\/01\/\u0443\u0431_0.png","link":"https:\/\/www.bigdataschool.ru\/blog\/biometrics-cybersecurity-big-data-leaks.html","title":"Cybersecurity Big Data: \u0441\u0430\u043c\u044b\u0435 \u043a\u0440\u0443\u043f\u043d\u044b\u0435 \u0443\u0442\u0435\u0447\u043a\u0438 \u0431\u0438\u043e\u043c\u0435\u0442\u0440\u0438\u0447\u0435\u0441\u043a\u0438\u0445 \u0434\u0430\u043d\u043d\u044b\u0445","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.4mRn3SB_WvotqLjyHYTE5gHaEH&pid=15.1","size":"668 x 372 \u00b7 png","desc":"","filetype":"png","width":668,"height":372,"domain":"www.bigdataschool.ru","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about campus fp vistalegre big data & cybersecurity technology Data technology futuristic advanced woman business big master mining concept cyber security role china analytics predictive cybersecurity unity3d college fba. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.







