big data protection technology All you need to know about the top 5 datacenter security solutions
If you are searching about Pin on Online Privacy you’ve visit to the right place. We have 9 Images about Pin on Online Privacy like All You Need to Know About The Top 5 Datacenter Security Solutions, Let’s talk about Big Data Security – TASIL and also All You Need to Know About The Top 5 Datacenter Security Solutions. Read more:
Pin On Online Privacy

www.pinterest.com
Big Data Protection Stock Vector. Illustration Of Orange – 125755881

www.dreamstime.com
Big Data Protection, Portability, And Recovery – Commvault
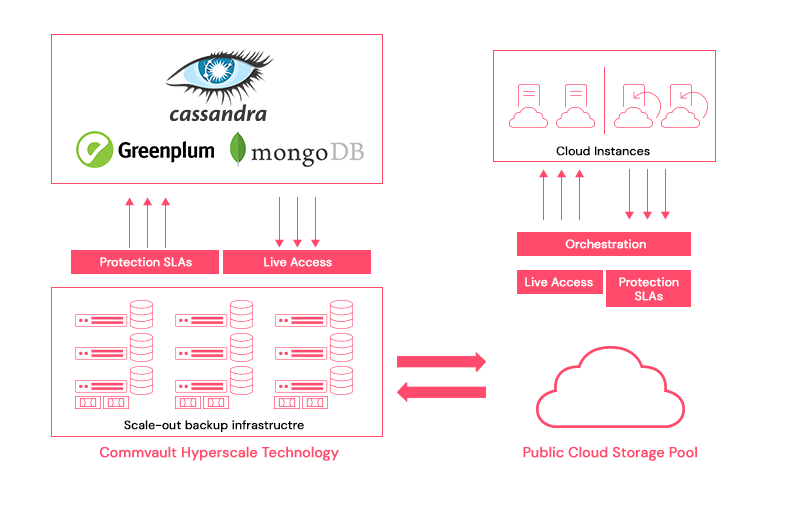
www.commvault.com
data big commvault recovery portability protection
Let’s Talk About Big Data Security – TASIL

tasil.com
tasil
Best Practices For Big Data Protection In Cloud

clouduts.com
All You Need To Know About The Top 5 Datacenter Security Solutions

www.eescorporation.com
DPOrganizer | Case Study | Polystar

www.dporganizer.com
data protection parts polystar study case big gdpr affects compliance almost very business been project
Big Data Security & Protection, Hadoop & IOT – SecureData | Micro Focus

software.microfocus.com
data big security
Technology Earth And Big Data Protection, Data Security And Storage

www.dreamstime.com
gateway
Technology earth and big data protection, data security and storage. Let’s talk about big data security. All you need to know about the top 5 datacenter security solutions
if you are looking "id":198,"keyword_id":null,"name":"big data protection technology","scraped_at":"2023-03-11 07:57:06","created_at":"2023-03-11T07:57:01.000000Z","updated_at":"2023-03-11T07:57:06.000000Z","images":["id":1792,"keyword_id":198,"url":"https:\/\/www.eescorporation.com\/wp-content\/uploads\/2021\/05\/big-data-security-1-1.jpg","link":"https:\/\/www.eescorporation.com\/datacenter-security-solutions\/","title":"All You Need to Know About The Top 5 Datacenter Security Solutions","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.5vZdpkuBev5bAtccIsTPdAHaGK&pid=15.1","size":"1000 x 833 \u00b7 jpeg","desc":"","filetype":"jpg","width":1000,"height":833,"domain":"www.eescorporation.com","created_at":null,"updated_at":null,"id":1793,"keyword_id":198,"url":"https:\/\/tasil.com\/wp-content\/uploads\/2019\/11\/Blog_16_00.jpg","link":"https:\/\/tasil.com\/insights\/big-data-security\/","title":"Let\u2019s talk about Big Data Security – TASIL","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.Hkpw7IGhLueOWBSts7CBvQHaEK&pid=15.1","size":"1920 x 1080 \u00b7 jpeg","desc":"tasil","filetype":"jpg","width":1920,"height":1080,"domain":"tasil.com","created_at":null,"updated_at":null,"id":1794,"keyword_id":198,"url":"https:\/\/clouduts.com\/wp-content\/uploads\/2020\/04\/big-data-protection.jpg","link":"https:\/\/clouduts.com\/big-data-protection-in-cloud\/","title":"Best Practices for Big Data Protection in Cloud","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.OXG8YWUxA-tc1gVthV7wWwHaD4&pid=15.1","size":"600 x 315 \u00b7 jpeg","desc":"","filetype":"jpg","width":600,"height":315,"domain":"clouduts.com","created_at":null,"updated_at":null,"id":1795,"keyword_id":198,"url":"https:\/\/thumbs.dreamstime.com\/z\/represents-global-big-data-protection-security-data-protection-program-design-technology-earth-big-data-protection-181765195.jpg","link":"https:\/\/www.dreamstime.com\/represents-global-big-data-protection-security-data-protection-program-design-technology-earth-big-data-protection-image181765195","title":"Technology Earth and Big Data Protection, Data Security and Storage","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.jHA2kKTt7rv1mej5OnLd7QHaGL&pid=15.1","size":"1600 x 1335 \u00b7 jpeg","desc":"gateway","filetype":"jpg","width":1600,"height":1335,"domain":"www.dreamstime.com","created_at":null,"updated_at":null,"id":1796,"keyword_id":198,"url":"https:\/\/9b74456f2e4bcbc20970-51751c7e8fb38e7c8b474cab6c7dc602.ssl.cf5.rackcdn.com\/2018-03\/eBook.png","link":"https:\/\/software.microfocus.com\/en-us\/products\/voltage-data-encryption-security\/features","title":"Big Data Security & Protection, Hadoop & IOT – SecureData ,"id":1797,"keyword_id":198,"url":"https:\/\/thumbs.dreamstime.com\/z\/big-data-protection-tiny-people-characters-around-shield-isolated-white-background-vector-dynamic-flat-design-business-125755881.jpg","link":"https:\/\/www.dreamstime.com\/big-data-protection-tiny-people-characters-around-shield-isolated-white-background-vector-dynamic-flat-design-business-image125755881","title":"Big Data Protection stock vector. Illustration of orange – 125755881","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.0WtK36QiL51NtpmJBlIXUgHaH0&pid=15.1","size":"1600 x 1690 \u00b7 jpeg","desc":"","filetype":"jpg","width":1600,"height":1690,"domain":"www.dreamstime.com","created_at":null,"updated_at":null,"id":1798,"keyword_id":198,"url":"https:\/\/i.pinimg.com\/originals\/7d\/c1\/8f\/7dc18fb79c608bf6151094226342c4c1.jpg","link":"https:\/\/www.pinterest.com\/pin\/197384396153963792\/","title":"Pin on Online Privacy","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.fXPVa_XHA-WKIy8PZvJOUwHaHa&pid=15.1","size":"582 x 582 \u00b7 jpeg","desc":"","filetype":"jpg","width":582,"height":582,"domain":"www.pinterest.com","created_at":null,"updated_at":null,"id":1799,"keyword_id":198,"url":"https:\/\/www.commvault.com\/wp-content\/uploads\/2019\/08\/2.png?w=788","link":"https:\/\/www.commvault.com\/protect-big-data","title":"Big Data Protection, Portability, And Recovery – Commvault","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.puFMB7WLjIB5vMqyB9mIOwHaEv&pid=15.1","size":"788 x 505 \u00b7 png","desc":"data big commvault recovery portability protection","filetype":"png","width":788,"height":505,"domain":"www.commvault.com","created_at":null,"updated_at":null, Polystar","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.uWGa4DRjL8GnHtUQhGoIEwAAAA&pid=15.1","size":"278 x 300 \u00b7 png","desc":"data protection parts polystar study case big gdpr affects compliance almost very business been project","filetype":"png","width":278,"height":300,"domain":"www.dporganizer.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about big data protection technology All you need to know about the top 5 datacenter security solutions. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.







