What new : edge computing benefits

Well hello there pals, you know what’s really cool? Edge Computing! That’s right, you may have heard of it before, but let me enlighten you on this amazing topic. First up, we’ve got this fancy image titled “What is Edge Computing?”
What is Edge Computing?
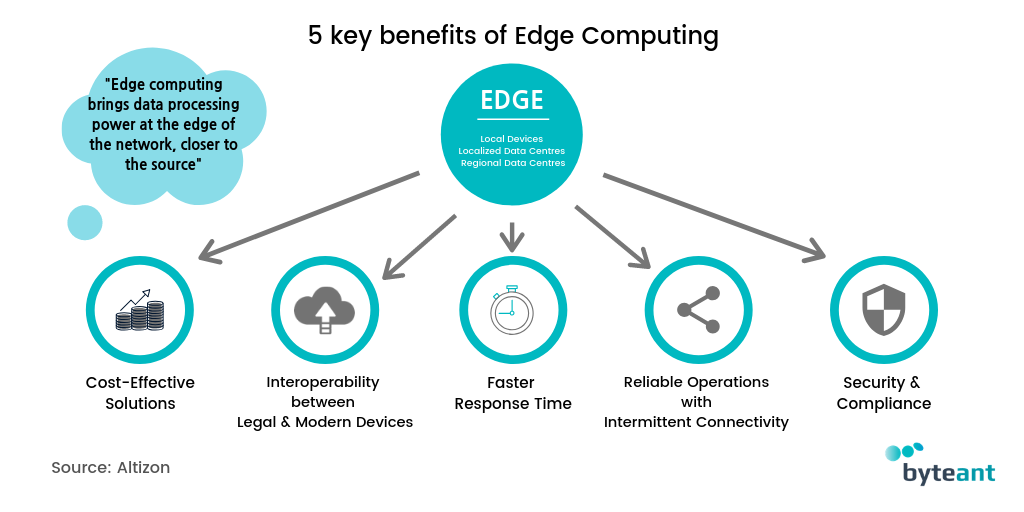
So basically, Edge Computing is a decentralized method of processing data and information by bringing computational power closer to where the data is generated. That’s right, we’re talking about pushing the computing power to the “edge” of the network, hence the name, “Edge Computing.”
Why is this cool, you may ask? Well, for starters, it helps reduce network latency and bandwidth usage. It also enables real-time data processing and analysis, which is crucial for applications such as self-driving cars and the Internet of Things (IOT).
But wait, there’s more! With Edge Computing, there’s less dependence on the cloud and centralized data centers, reducing the risk of downtime caused by network congestion or failures. So, it’s not just cool, it’s also a pretty reliable method of processing and managing data.
Privacy Enhancing Technologies
Now, here’s an image that caught my attention, titled “Top Ten Privacy Enhancing Technologies.”
Privacy is a big deal these days, and that’s where “Privacy Enhancing Technologies” (PETs) come in. PETs are a set of technologies that are designed to help protect people’s privacy and personal data.
Abstract
The intersection of Edge Computing and Privacy Enhancing Technologies is becoming increasingly important in today’s connected world. This article aims to explore the ways in which Edge Computing can be used to enhance privacy, particularly in the context of the Internet of Things (IOT).
Introduction
With the proliferation of connected devices, the need for privacy-enhancing technologies has never been greater. IOT devices generate massive amounts of data, which can be vulnerable to attacks or misuse, putting people’s personal information at risk.
Edge Computing has the potential to address some of the privacy concerns associated with IOT devices by reducing the amount of data that needs to be sent to the cloud, and by processing data locally. This article will explore the ways in which Edge Computing can be used to enhance privacy, particularly in the context of IOT devices.
Content
Reducing Data Exposure
One of the primary ways in which Edge Computing can enhance privacy is by reducing the amount of data that needs to be sent to the cloud. With traditional cloud-based computing models, much of the data generated by IOT devices is sent to a centralized location for analysis and processing. This means that all the data generated by the device is exposed, which increases the risk of privacy violations.
Edge Computing, on the other hand, allows for data to be processed locally, which means that only the necessary data needs to be sent to the cloud. This reduces the risk of exposure and minimizes the amount of data that is vulnerable to breaches.
Data Inference
Another way in which Edge Computing can enhance privacy is by minimizing the amount of data that needs to be analyzed in the cloud. With traditional cloud-based computing models, all data generated by IOT devices needs to be sent to the cloud for processing, which can be time-consuming and expensive.
Edge Computing allows for data to be processed locally, which means that only relevant data needs to be sent to the cloud. This can help to reduce costs and processing time, and can allow for a more efficient analysis of data.
Local Data Processing
Edge Computing enables data to be processed on local devices, which can be much faster than relying on cloud-based processing. This means that real-time data analysis and processing can occur on local devices, providing faster response times and enabling real-time decision making.
This is particularly important in situations where split-second decisions need to be made, such as in autonomous vehicles, industrial automation, and medical devices. By processing data locally, Edge Computing can help to ensure that these decisions are made quickly and effectively, which can ultimately save lives and increase productivity.
Data Encryption
Edge Computing also enables data to be encrypted locally, which can help to enhance privacy and protect against data breaches. By encrypting data at the Edge, data is protected from prying eyes, and can only be decrypted when it is processed in the cloud.
This means that even if data is intercepted, it will be unreadable, reducing the risk of privacy violations. Edge Computing also enables device-level key management, which can help to further strengthen security measures and protect against attacks.
Conclusion
Edge Computing has the potential to revolutionize the way we process and manage data, and it can also enhance privacy and security measures. By bringing processing power closer to where data is generated, Edge Computing can reduce the amount of data that needs to be sent to the cloud, minimizing the risk of privacy violations.
Edge Computing can also enable real-time data analysis and processing, providing faster response times and enabling split-second decision-making. With Edge Computing, data can be encrypted locally, protecting against data breaches and strengthening security measures.
The intersection of Edge Computing and Privacy Enhancing Technologies is becoming increasingly important in today’s connected world, and it will be exciting to see how these technologies develop in the years to come.
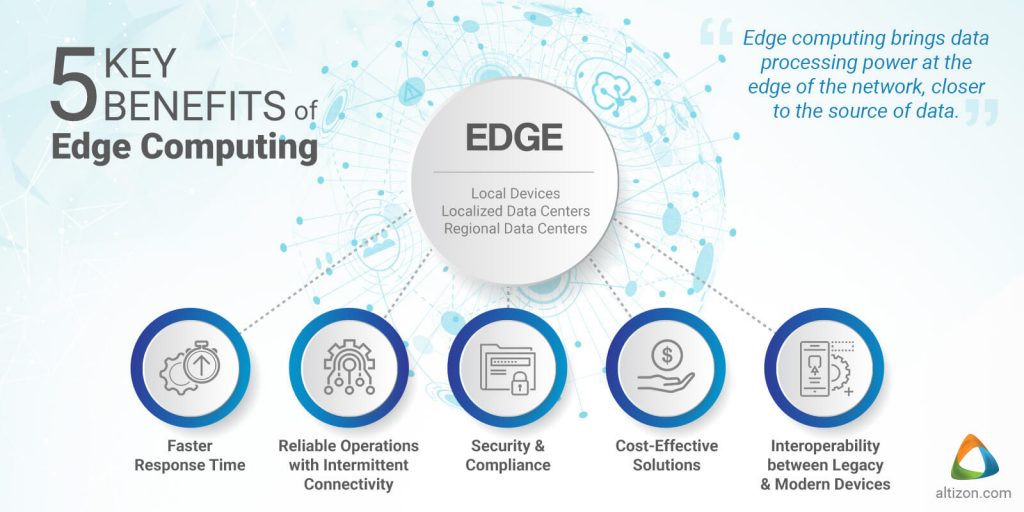
Source image : altizon.com

Source image : www.trentonsystems.com

Source image : www.techyv.com


