cloud computing guidance Cloud security guidance computing critical areas focus v2 alliance
If you are looking for Security Guidance Critical Areas of Focus Cloud Computing V2.1 – Cloud you’ve came to the right page. We have 9 Images about Security Guidance Critical Areas of Focus Cloud Computing V2.1 – Cloud like Security Guidance Resources | CSA, Security Guidance Critical Areas of Focus Cloud Computing V2.1 – Cloud and also NIST Issues Public Cloud Computing Guidance – BankInfoSecurity. Here you go:
Security Guidance Critical Areas Of Focus Cloud Computing V2.1 – Cloud
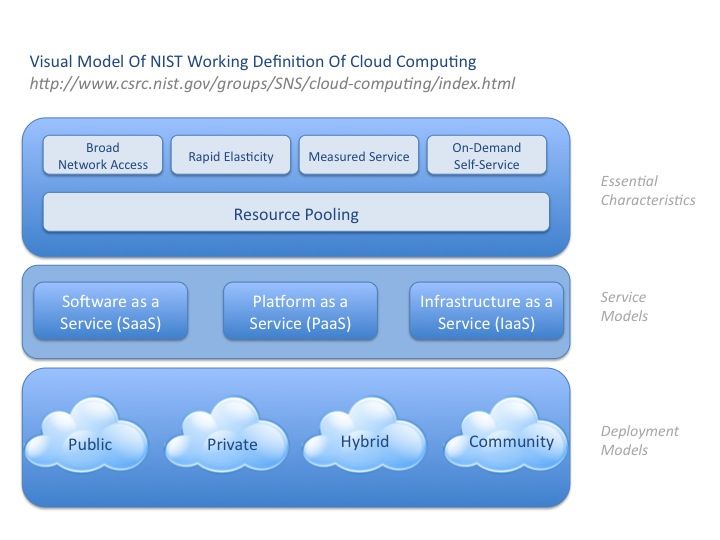
www.readkong.com
NIST Issues Public Cloud Computing Guidance – BankInfoSecurity

www.bankinfosecurity.com
Cloud Computing Guidance For Organisations Ashx By Roseberry Academy

issuu.com
Security Guidance Critical Areas Of Focus Cloud Computing V2.1 – Cloud
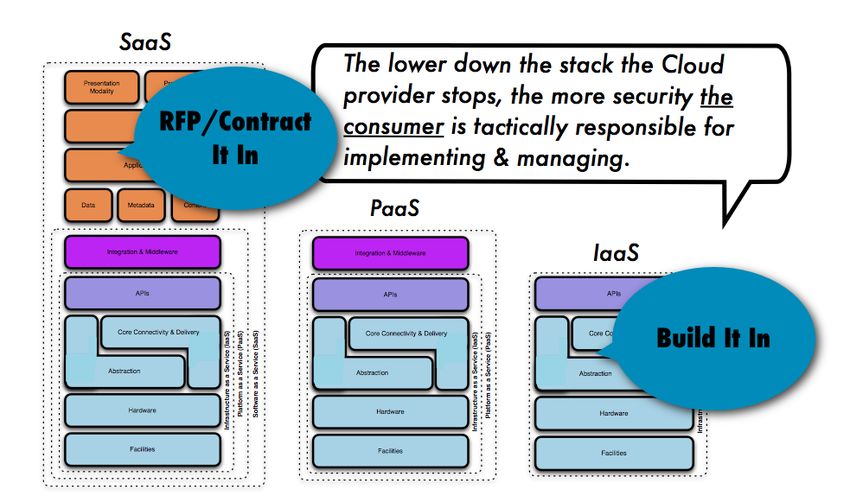
www.readkong.com
cloud security guidance computing critical areas focus v2 alliance
Security Guidance Resources | CSA

cloudsecurityalliance.org
FFIEC Outsourced Cloud Computing Guidance Overview | CoNetrix

conetrix.com
cloud computing ffiec outsourced guidance overview
Cloud Computing Training Institutes In Chennai – Software Testing

www.gcreddy.com
computing cloud training institutes chennai
Challenges And Risks In Cloud Computing

geekflare.com
cloud computing geekflare risks challenges involves
Cloud Computing For Beginners: Some Guidance Regarding Its’ Functioning

www.girikon.com.au
computing guidance regarding functioning aspects various
Cloud security guidance computing critical areas focus v2 alliance. Cloud computing training institutes in chennai. Cloud computing for beginners: some guidance regarding its’ functioning
if you are looking "id":239,"keyword_id":null,"name":"cloud computing guidance","scraped_at":"2023-03-12 18:37:20","created_at":"2023-03-12T18:37:17.000000Z","updated_at":"2023-03-12T18:37:20.000000Z","images":[ CSA","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.IOuFF3Rv97wKrDZzuPN6XQAAAA&pid=15.1","size":"420 x 547 \u00b7 png","desc":"","filetype":"png","width":420,"height":547,"domain":"cloudsecurityalliance.org","created_at":null,"updated_at":null,"id":2126,"keyword_id":239,"url":"https:\/\/www.readkong.com\/static\/42\/44\/424452d9808914a81a70205354dbe767\/security-guidance-critical-areas-of-focus-cloud-computing-9011677-3.jpg","link":"https:\/\/www.readkong.com\/page\/security-guidance-critical-areas-of-focus-cloud-computing-9011677","title":"Security Guidance Critical Areas of Focus Cloud Computing V2.1 – Cloud","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.uw0npgWyeXSJPU1uhX6F_wHaEX&pid=15.1","size":"850 x 502 \u00b7 jpeg","desc":"cloud security guidance computing critical areas focus v2 alliance","filetype":"jpg","width":850,"height":502,"domain":"www.readkong.com","created_at":null,"updated_at":null,"id":2127,"keyword_id":239,"url":"https:\/\/130e178e8f8ba617604b-8aedd782b7d22cfe0d1146da69a52436.ssl.cf1.rackcdn.com\/nist-issues-public-cloud-computing-guidance-imageFile-a-4438.jpg","link":"https:\/\/www.bankinfosecurity.com\/nist-issues-public-cloud-computing-guidance-a-4438","title":"NIST Issues Public Cloud Computing Guidance – BankInfoSecurity","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.SC22BPg3tgm_i5c46H3sGAHaHf&pid=15.1","size":"173 x 175 \u00b7 jpeg","desc":"","filetype":"jpg","width":173,"height":175,"domain":"www.bankinfosecurity.com","created_at":null,"updated_at":null,"id":2128,"keyword_id":239,"url":"https:\/\/www.girikon.com.au\/wp-content\/uploads\/2020\/05\/Cloud-computing-for-beginners-Some-Guidance-Regarding-its-functioning-in-the-Digital-Era.png","link":"https:\/\/www.girikon.com.au\/blog\/cloud-computing-for-beginners-some-guidance-regarding-its-functioning-in-the-digital-era\/","title":"Cloud computing for beginners: Some Guidance Regarding its\u2019 functioning","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.uYvsfS-vUnTazMB_OwwRawHaEi&pid=15.1","size":"543 x 333 \u00b7 png","desc":"computing guidance regarding functioning aspects various","filetype":"png","width":543,"height":333,"domain":"www.girikon.com.au","created_at":null,"updated_at":null,"id":2129,"keyword_id":239,"url":"https:\/\/www.gcreddy.com\/wp-content\/uploads\/2018\/08\/Cloud-Computing.jpg","link":"https:\/\/www.gcreddy.com\/2017\/07\/cloud-computing-training-institutes-in-chennai.html","title":"Cloud Computing Training Institutes In Chennai – Software Testing","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.AZETpsVCCfTr8xHIa3yyAQHaEK&pid=15.1","size":"1280 x 720 \u00b7 jpeg","desc":"computing cloud training institutes chennai","filetype":"jpg","width":1280,"height":720,"domain":"www.gcreddy.com","created_at":null,"updated_at":null,"id":2130,"keyword_id":239,"url":"https:\/\/geekflare.com\/wp-content\/uploads\/2021\/12\/cloudcomputing1.png","link":"https:\/\/geekflare.com\/challenges-and-risks-in-cloud-computing\/","title":"Challenges and Risks in Cloud Computing","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.zEAYRtKXJYaMA3a1QydWhgHaC9&pid=15.1","size":"1000 x 400 \u00b7 png","desc":"cloud computing geekflare risks challenges involves","filetype":"png","width":1000,"height":400,"domain":"geekflare.com","created_at":null,"updated_at":null,"id":2131,"keyword_id":239,"url":"https:\/\/image.isu.pub\/150513110115-05b8a3de03ff35813bd645b8959ac673\/jpg\/page_1.jpg","link":"https:\/\/issuu.com\/roseberryacademy\/docs\/cloud_computing_guidance_for_organi","title":"Cloud computing guidance for organisations ashx by Roseberry Academy","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.Hg76hgC80w2MdNMdiyqPCAHaKe&pid=15.1","size":"1058 x 1497 \u00b7 jpeg","desc":"","filetype":"jpg","width":1058,"height":1497,"domain":"issuu.com","created_at":null,"updated_at":null, CoNetrix","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.ThqPY-oDQkn7PgwxLPr_8wAAAA&pid=15.1","size":"200 x 260 \u00b7 png","desc":"cloud computing ffiec outsourced guidance overview","filetype":"png","width":200,"height":260,"domain":"conetrix.com","created_at":null,"updated_at":null,"id":2133,"keyword_id":239,"url":"https:\/\/www.readkong.com\/static\/42\/44\/424452d9808914a81a70205354dbe767\/security-guidance-critical-areas-of-focus-cloud-computing-9011677-2.jpg","link":"https:\/\/www.readkong.com\/page\/security-guidance-critical-areas-of-focus-cloud-computing-9011677","title":"Security Guidance Critical Areas of Focus Cloud Computing V2.1 – Cloud","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.23Fv1Njp1_WQg6uwZNyV7QHaFj&pid=15.1","size":"720 x 540 \u00b7 jpeg","desc":"","filetype":"jpg","width":720,"height":540,"domain":"www.readkong.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about cloud computing guidance Cloud security guidance computing critical areas focus v2 alliance. Don’t forget to bookmark this page for future reference or share to facebook / twitter if you like this page.






